In security, nothing is “unhackable.” When it’s claimed, security researchers see nothing more than a challenge.
Enter the latest findings from Pen Test Partners, a U.K.-based cybersecurity firm. Their latest project was ripping apart the “unhackable” eyeDisk, an allegedly secure USB flash drive that uses iris recognition to unlock and decrypt the device.
eyeDisk raised over $21,000 in its Kickstarter campaign last year and began shipping devices in March.
There’s just one problem: it’s anything but “unhackable.”
Pen Test Partners researcher David Lodge found the device’s backup password — to access data in the event of device failure or a sudden eye-gouging accident — could be easily obtained using a software tool able to sniff USB device traffic.
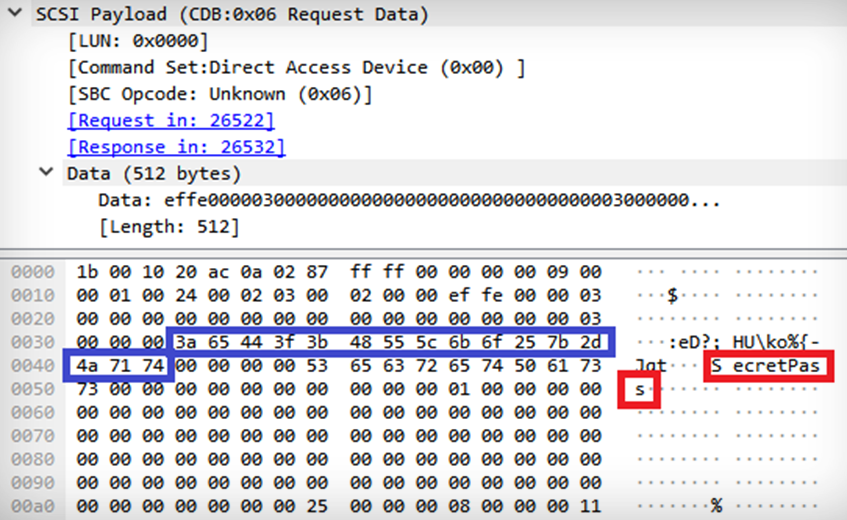
The secret password — “SecretPass” — can be seen in plaintext. (Image: Pen Test Partners)
“That string in red, that’s the password I set on the device. In the clear. Across an easy to sniff bus,” he said in a blog post detailing his findings. The password is
Worse, he said, the device’s real password can be picked up even when the wrong password has been entered. Lodge explained this as the device revealing its password first, then validating it against whatever password the user submitted before the unlock password is sent.
Lodge said anyone using one of these devices should use additional encryption on the device.
The researcher disclosed the flaw to eyeDisk, which promised a fix, but has yet to release it. eyeDisk did not return a request for comment.
0 Comments
Post a Comment