More than 1.5 million users of a group dating service had their personal data exposed — including their real-time location — because of a vulnerability in the app.
The app, 3fun, bills itself as a “private space” where you can meet “local kinky, open-minded people.” But the data wasn’t private at all. Ken Munro, founder of Pen Test Partners, which published the research Thursday and shared its findings with TechCrunch, said it was “probably the worst security for any dating app we’ve ever seen.”
Pen Test Partners researchers found the app was leaking the precise location, photos and other personal details of any nearby user.
Worse, because the app wasn’t properly secured, the researchers found they could plug in any coordinates they wanted to spoof their location, revealing sensitive information on anyone within any location of their choosing, including government buildings, military bases, and even intelligence agencies.
TechCrunch ran the same tests as Pen Test Partners and confirmed its findings. We were able to modify our current geolocation to any set of coordinates we wanted — including the White House and the CIA.
Using a man-in-the-middle tool like Burp Suite, we could capture our real location, manipulate it in transit on the way to the server, and receive a batch of data for that location.
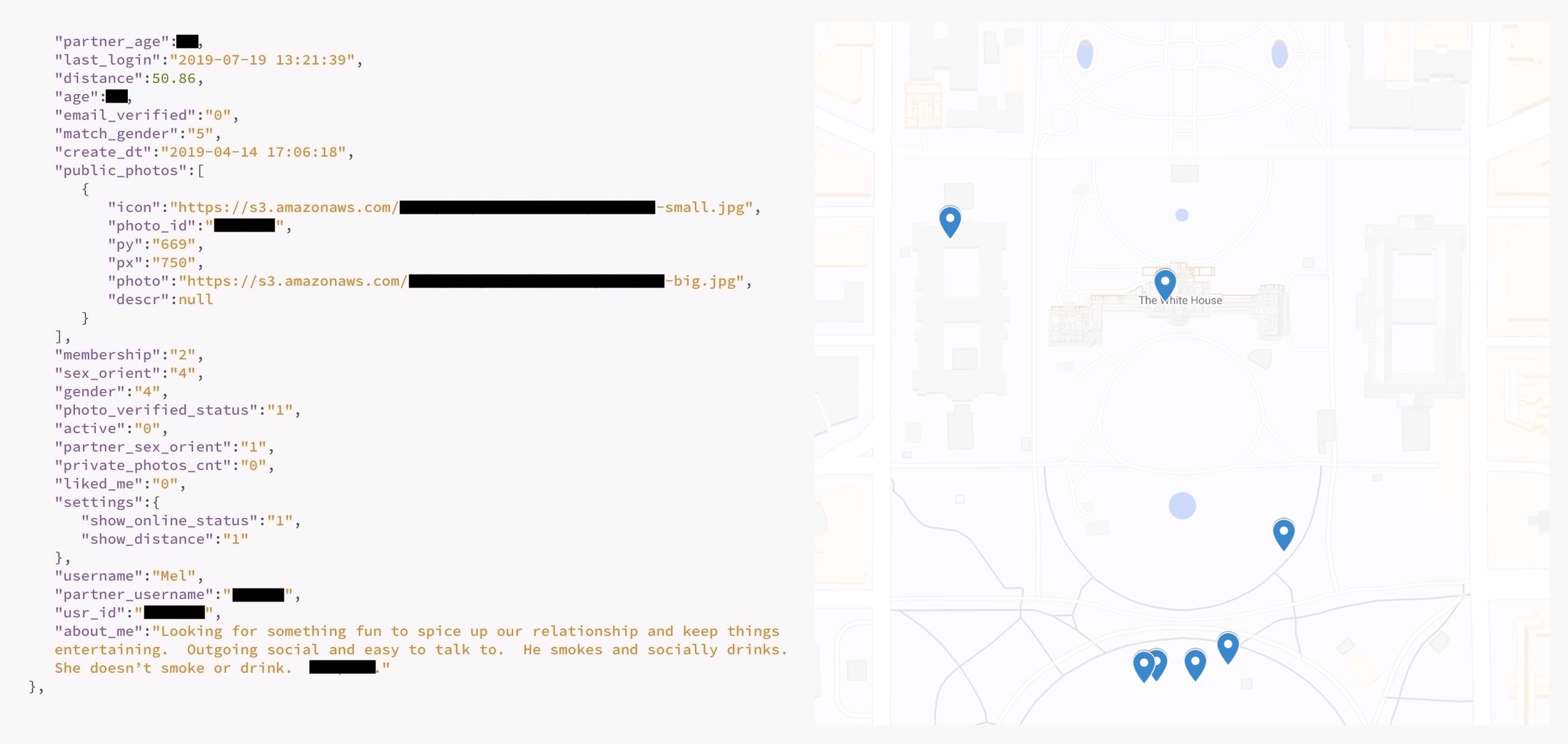
One of the exposed user records (left) and an approximate representation of several users (right).
We found profiles of users at both locations, including their sexual preferences — including sexual orientation and their preferred matches; their age; username and their partner’s username; their bio — many of which included expansive, specific and personal information on the user; and their full-resolution profile picture. In some cases, dates of birth were also exposed.
None of the data was encrypted. The researchers called the app a “privacy train wreck.”
The researchers contacted 3fun on July 1 to report the bugs. Munro said the app maker took weeks to fix the issues.
We emailed 3fun with several questions, but spokesperson Jennifer White did not respond to a request for comment.
It’s the latest app to fall foul of proper security standards in recent months. Jewish dating app JCrush left 200,000 user records exposed in June following a security lapse. Last year on its launch day, conservative dating app Donald Daters exposed its entire user base — at the time some 1,600 users — after leaving a set of hardcoded keys in its app, which was quickly found after a security researcher decompiled the app.
Another dating app, Coffee Meets Bagel, was breached on Valentine’s Day, no less.
Well, that’s one way to a person’s heart — hacking their dating profile.

0 Comments
Post a Comment